In today’s digital age, with just a few taps on your smartphone, you can take a stunning snapshot, enhance it with filters, and share it with the world. One of the powerful features that modern devices offer is geotagging, which automatically embeds location data into your photos. This feature adds a layer of context, making it simple to remember where your cherished memories were made. However, while geotagging offers convenience and a richer storytelling experience, it also introduces a host of privacy and security risks. This article aims to provide you a clear view of risks associated with geotagging in snapshots and suggest some potential ways to minimize them.
What is Geotagging in Snapshots?

Geotagging in snapshots refers to the process of adding geographical information to the metadata of a photograph. This geographical information typically includes the exact coordinates (latitude and longitude) where the photo was taken, and it can also include altitude, bearing, and other location-specific data.
How Geotagging Works
GPS Integration
- GPS Technology: Most modern smartphones and digital cameras come equipped with GPS (Global Positioning System) receivers. These devices can determine their precise location on Earth using signals from a network of satellites.
- Location Data: When a photo is taken, the device’s GPS receiver calculates the location data, which includes latitude, longitude, and sometimes altitude. This calculation involves triangulating the position based on signals received from at least three GPS satellites.
Capturing a Photo
- Photo Capture: When you take a photo, the camera or smartphone captures the image data.
- Simultaneous Location Capture: At the same time, the device’s GPS receiver captures the current geographical coordinates.
Embedding Metadata
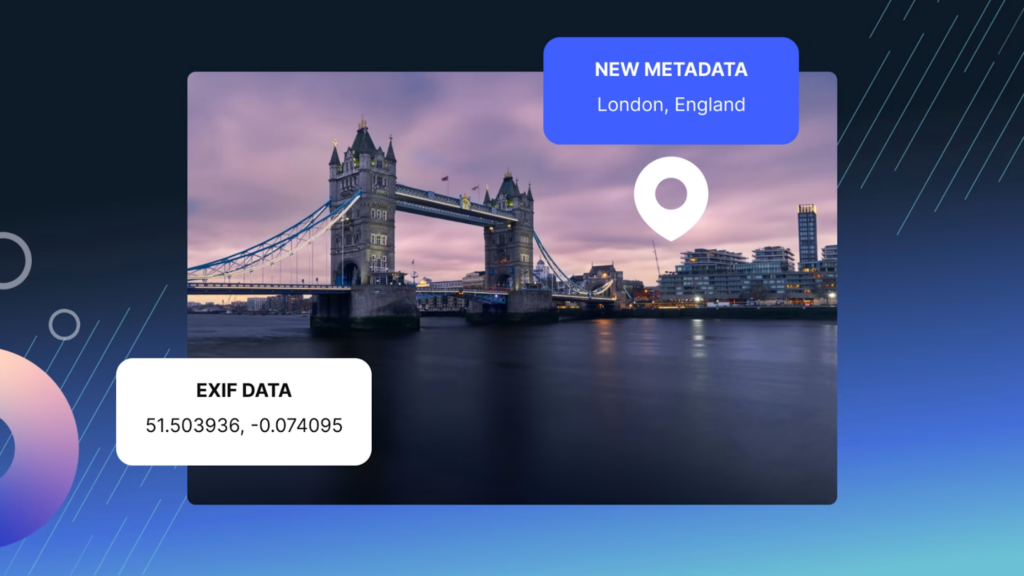
- EXIF Metadata: The device embeds the geographical information into the photo’s EXIF (Exchangeable Image File Format) metadata. EXIF metadata is a standard format that stores a variety of details about the photo, such as:
- Camera Settings: Shutter speed, aperture, ISO, etc.
- Date and Time: The exact time the photo was taken.
- Geolocation Data: Latitude, longitude, altitude, and sometimes the direction (bearing) the camera was facing.
Software and Apps
- Metadata Reading: Various software applications and photo management apps can read the EXIF metadata. These include photo editing programs, social media platforms, and photo organization apps.
- Mapping and Organization: Apps like Google Photos, Apple Photos, and Flickr can use the geolocation data for map view, location-based albums and search by location.
Risks of Geotagging in Snapshots
Although geotagging can bring various benefits in terms of travel, memory recall, mapping and analysis, it still implies a great number of risks.
Let’s discover with us the risks of geotagging in snapshots:
Privacy Invasion
- Routine Tracking: By analyzing geotagged photos, someone could determine your daily routines, favorite places, or commonly visited locations. This can make it easier for someone to predict where you might be at any given time.
- Home Address Exposure: Photos taken at home and shared publicly can reveal your home address. This is particularly concerning if your address is supposed to be private.
- Historical Data Compilation: Over time, a series of geotagged photos can create a comprehensive history of your movements, offering insights into your life that you might not wish to share.
Safety Concerns

- Stalking and Harassment: Individuals with malicious intent can use geotagged information to follow or harass you, knowing where you are or have been recently.
- Domestic Violence: For victims of domestic violence or stalking, geotagged photos can inadvertently reveal their location to their abusers.
- Children’s Safety: Parents might share photos of their children at school, parks, or other locations, inadvertently exposing these locations to potential predators.
Property Theft
- Vacation Posts: Sharing photos while on vacation can signal to burglars that your home is currently unoccupied. This increases the risk of break-ins during your absence.
- Pattern Recognition: Regular posting of geotagged photos can reveal patterns, such as when you are usually away from home, which burglars can exploit.
Data Misuse
- Targeted Advertising: Companies can use location data from geotagged photos to deliver highly targeted ads. While this might seem benign, it can feel intrusive and like a violation of privacy.
- Profile Building: Data aggregators can compile detailed profiles based on your geotagged photos, which can then be sold to third parties. This information can be used for various purposes, including targeted marketing, without your consent.
- Location-Based Surveillance: Continuous tracking of location data can lead to a feeling of being constantly watched and monitored, impacting your sense of privacy.
Unintended Disclosure
- Military and Sensitive Locations: Photos taken at sensitive locations like military bases or government facilities can reveal details that should remain confidential, posing a risk to national security.
- Confidential Business Sites: Employees taking geotagged photos at work can inadvertently disclose the location of business operations, client sites, or sensitive projects, leading to potential business risks.
Social Engineering
- Phishing Attacks: Malicious actors can use location data to craft personalized phishing emails that reference specific places you’ve visited, making the attacks more convincing.
- Identity Theft: By gathering information from geotagged photos, criminals can piece together details about your life, which can be used in identity theft schemes.
- Baiting and Impersonation: Knowing your routine and frequently visited places can enable attackers to impersonate you or someone you know, creating more effective social engineering attacks.
How to Minimize Risks of Geotagging in Snapshots
To minimize the risks associated with geotagging in snapshots, you can take several proactive steps to manage the location data embedded in your photos.
Here are some of recommended strategies to minimize risks of geotagging in snapshots:
Tip 1: Disable Geotagging
- Smartphone Settings: Turn off the geotagging feature on your smartphone or camera.
- iPhone: Go to Settings > Privacy > Location Services, then find your camera app and select Never or While Using the App.
- Android: Go to Settings > Location > App permissions, then find your camera app and turn off location access.
- Camera Settings: For digital cameras with built-in GPS, refer to the user manual to disable geotagging in the settings menu.
Tip 2: Review and Remove Metadata
- Metadata Removal Tools: Use software tools to review and remove EXIF metadata before sharing photos.
- Windows: Right-click the photo file, select Properties > Details, and click Remove Properties and Personal Information.
- Mac: Use Preview to open the photo, then go to Tools > Show Inspector > Info, and remove location data.
- Online Tools: Websites like metapicz.com and verexif.com allow you to view and remove metadata from photos.
Tip 3: Configure Social Media Settings
- Social Media Platforms: Adjust settings on social media platforms to control the sharing of location data.
- Facebook: When posting a photo, click on the location icon and remove any tagged location on Facebook.
- Instagram: Ensure that the Add Location option is unchecked when posting a photo. You can also remove location data from previously posted photos by editing the post on Instagram.
Tip 4: Use Privacy Settings
- Photo Sharing Apps: Use privacy settings to control who can see your photos.
- Google Photos: Share albums with specific people instead of making them public. Turn off location sharing in settings.
- Apple Photos: Use the Shared Albums feature to share photos privately with selected individuals. Ensure Include Location is turned off in shared album settings.
- Custom Privacy Settings: Many platforms allow you to create custom privacy settings, so only friends or specific groups can see your geotagged photos.
Tip 5: Be Mindful of Sharing
- Delayed Sharing: Avoid sharing photos with geotags in real-time. Wait until you have left the location to post.
- Selective Sharing: Only share geotagged photos with trusted individuals or groups. Consider using private messaging apps for sharing sensitive photos.
- Blur Sensitive Locations: For photos taken in or around sensitive locations, consider using photo editing tools to blur out identifiable landmarks or features.
Tip 6: Use Geotagging Alternatives

- Manual Tagging: Instead of automatic geotagging, consider manually adding location information to photos only when necessary.
- Virtual Locations: Use generic or non-specific locations for tagging if you want to include some location context without revealing exact coordinates.
Conclusion
Geotagging in snapshots is a double-edged sword, offering both enhanced memories and significant privacy risks. In a time where our lives are increasingly documented and shared online, understanding and managing the implications of geotagging is more important than ever. By following the guidance provided in this article, you can strike a balance between sharing your experiences and safeguarding your privacy.
About Herond Browser
Herond Browser is a Web browser that prioritizes users’ privacy by blocking ads and cookie trackers, while offering fast browsing speed and low bandwidth consumption. Herond Browser features two built-in key products:
- Herond Shield: an adblock and privacy protection tool;
- Herond Wallet: a multi-chain, non-custodial social wallet.
Herond aims at becoming the ultimate Web 2.5 solution that sets the ground to further accelerate the growth of Web 3.0, heading towards the future of mass adoption.
Join our Community!