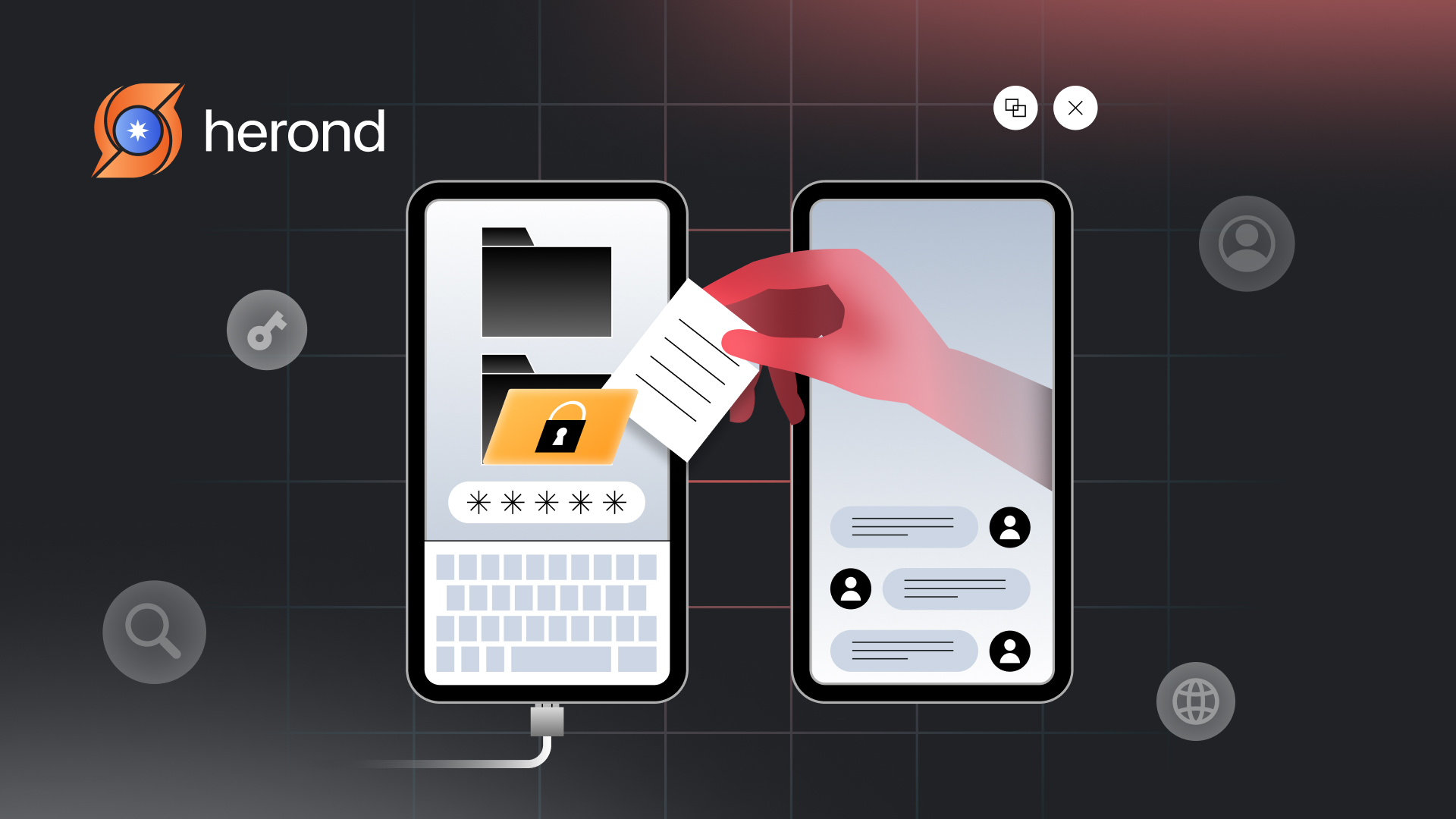
In the world of digital life, our devices are treasure troves of personal and sensitive information, from financial records to private communications. However, this wealth of data makes them prime targets for cybercriminals and hackers. Internet leak – whether through malware, phishing scams, or unsecured connections, poses significant threats to our privacy and security. Fortunately, there are effective strategies you can implement to safeguard your devices against these risks. In this article, we’ll explore the top 10 ways to prevent internet leak, ensuring that your information remains protected and your online activities stay private. By following these practical tips, you can bolster your defenses and navigate the digital world with confidence.
What is Internet Leak?
An internet leak typically refers to the unauthorized or accidental exposure of sensitive information, such as personal data, financial records, confidential business information, or intellectual property, over the internet. This exposure can occur in various forms and can have serious consequences for individuals, businesses, and organizations.
Types of Internet Leak
Data Breaches
Unauthorized access to a system or network leading to the exposure of sensitive information. Examples include hacking incidents where personal data like names, addresses, credit card numbers, or social security numbers are stolen.
Accidental Leaks
Human error or misconfiguration can lead to accidental exposure of data. For example, mistakenly sending an email with sensitive attachments to the wrong recipient or inadvertently posting confidential information on a public website.
Insider Leaks
Employees or other insiders intentionally or unintentionally sharing confidential information. This can occur due to negligence, lack of awareness, or malicious intent.
Cloud Storage Leaks
Misconfigured cloud storage services can leave data exposed to unauthorized access. For instance, a publicly accessible cloud bucket containing private data.
Source Code Leaks
Unauthorized release of proprietary source code, which can lead to security vulnerabilities and intellectual property theft.
Document Leaks
Release of sensitive documents, such as government or corporate reports, that are not intended for public view.
Top 10 Ways to Prevent Internet Leak
Here are top 10 tips to prevent internet leak:
Tip 1: Use Data Encryption
Data encryption is a vital method for safeguarding sensitive information and preventing internet leak by converting readable data into an unreadable format, which can only be decrypted by authorized users. This process involves encrypting data both at rest (stored data) and in transit (data being transmitted over networks). For data at rest, encryption tools like BitLocker, FileVault, and cloud storage encryption services ensure that even if storage devices or cloud accounts are accessed by unauthorized individuals, the data remains protected. For data in transit, using protocols like TLS for web communications and VPNs for secure network connections ensures that data sent across networks cannot be intercepted and read by malicious entities.
Next, to effectively implement data encryption, organizations should also do some more actions as follows:
- Use Strong Encryption Algorithms: Employ industry-standard algorithms like AES-256 for robust security. This includes secure key storage, regular key rotation, and using key management services like AWS KMS to automate and control the encryption process. Moreover, it is noticeable to avoid deprecated algorithms such as DES or MD5, which are no longer considered secure.
- Ensure End-to-End Encryption: Implement encryption that protects data throughout its entire lifecycle, from creation to storage to transmission. For example, secure messaging apps like Signal use end-to-end encryption.
- Implement Encryption Policies: Develop and enforce policies for encryption use within your organization.
Tip 2: Enable Multi-Factor Authentication (MFA)
Enabling Multi-Factor Authentication (MFA) is a highly effective method to enhance security and prevent internet leak. MFA requires users to provide two or more verification factors to gain access to a resource such as an application, online account, or VPN. This layered approach makes it more difficult for unauthorized individuals to access your data.
Here are some popular MFA methods:
- Authenticator Apps: Apps like Google Authenticator, Microsoft Authenticator, or Authy generate time-based one-time passwords (TOTPs).
- SMS/Email Codes: Codes sent to your phone or email.
- Hardware Tokens: Physical devices like YubiKey.
- Biometric Authentication: Fingerprint or facial recognition on supported devices.
Tip 3: Use Strong, Unique Passwords and a Password Manager
Using strong, unique passwords in conjunction with a password manager is an effective way to prevent internet leak. Here’s a detailed guide on how to implement this strategy:
- Length: Aim for at least 12-16 characters.
- Complexity: Include a mix of letters, numbers, and symbols.
- Avoid Predictability: Don’t use easily guessable information like birthdays, names, or common words.
Example of a Strong Password: L8k@2#Yq!jF7tV3w
Moreover, you can use Password Manager to securely store and organize your passwords, making it easy to use strong, unique passwords for every account. Discover more about Google password manager.
Tip 4: Keep Your Software and Operating Systems Updated
Keeping your software and operating systems updated is a crucial step in preventing internet leak and ensuring the security of your devices due to:
- Security Patches: Updates often include patches for security vulnerabilities that could be exploited by attackers.
- Improved Functionality: Updates can improve the functionality and performance of your software and operating systems, providing a better user experience.
- Compatibility: Keeping your systems updated ensures compatibility with other software and services, reducing the risk of conflicts and security gaps.
- Bug Fixes: Updates fix bugs that could potentially cause crashes or other issues that might be exploited.
It is highly recommended that automatic updates are enabled for your operating system.
- Windows: Go to Settings > Update & Security > Windows Update, and ensure automatic updates are turned on.
- MacOS: Go to System Preferences > Software Update, and check “Automatically keep my Mac up to date.”
Tip 5: Be Cautious with Email and Phishing Scams
Phishing scams are designed to trick you into providing sensitive information such as passwords, credit card numbers, or other personal data. Here’s how to recognize, avoid, and handle phishing attempts:
- Suspicious Sender Address: Check the sender’s email address carefully. Phishers often use addresses that mimic legitimate ones but with slight variations.
- Urgent or Threatening Language: Phishing emails often create a sense of urgency or fear to prompt immediate action.
- Unusual Attachments or Links: Be wary of unexpected attachments or links, especially from unknown senders.
- Generic Greetings: Legitimate organizations usually address you by name. Be cautious of emails that use generic greetings like “Dear Customer.”
- Spelling and Grammar Errors: Many phishing emails contain noticeable spelling and grammar mistakes.
- Unusual Requests: Be cautious if the email requests sensitive information or asks you to verify your account details.
Tip 6: Regularly Back Up Your Data
Regularly backing up your data is a crucial strategy to prevent internet leak because it is useful for data recovery, protection against malware and accidental deletion.
Here are some common backup methods:
- Local Backups: Store backups on external hard drives, USB drives, or other physical media. This way offers fast recovery without internet needed, but it is exposed to high risk of physical damage or theft.
- Cloud Backups: Use cloud storage services to store backups offsite. It is accessible from anywhere, so protected from local disasters. However, it requires the internet, potentially leading to privacy concerns.
- Hybrid Approach: Combine local and cloud backups for comprehensive protection. It offers redundancy and multiple recovery options.
Tip 7: Use Secure Wi-Fi Connections
Using secure Wi-Fi connections is essential to prevent internet leaks and protect your personal information from unauthorized access. Here’s how to ensure your Wi-Fi connections are secure:
- Secure Your Home Wi-Fi Network: You should set a strong password, update router firmware, disable WPS and create a guest network to make sure your home wifi network is secure.
- Use a Virtual Private Network (VPN): Use a reputable VPN service to encrypt your internet connection. Moreover, always use a VPN when connecting to public Wi-Fi networks to protect your data from eavesdroppers.
Tip 8: Install and Update Antivirus/Anti-Malware Software
Installing and regularly updating antivirus and anti-malware software is crucial to prevent internet leak and protect your devices from malicious attacks. Here are some popular Antivirus/Anti-Malware Software including Norton Security, Kaspersky Total Security, Bitdefender, and Malwarebytes.
Tip 9: Configuring firewalls and Intrusion Detection Systems (IDS)
Configuring firewalls and Intrusion Detection Systems (IDS) is crucial to preventing internet leak and protecting your network from unauthorized access and malicious activities. There are two common types of firewalls, including:
- Network Firewalls: Protect the entire network by filtering incoming and outgoing traffic based on predefined security rules.
- Host-Based Firewalls: Installed on individual devices (e.g., computers, smartphones) to monitor and control network traffic specific to that device.
Tip 10: Educate ourselves with good understanding of internet leak
Using tools is not the key thing to help us away from the internet, but the most important note here is that we should educate ourselves about internet leak. It means that wisdom when being on the internet is crucial for us. Moreover, it is highly recommended that you should also share knowledge with your family, friends and colleagues about internet security risks and best practices.
Conclusion
In an era where our lives are increasingly intertwined with the digital world, protecting our personal and sensitive information is more important than ever. Internet leak can have devastating consequences, from identity theft to financial loss. However, by implementing the top 10 ways to prevent internet leak on your devices, you can significantly enhance your security posture, minimize the risk of internet leak and enjoy greater peace of mind.
About Herond Browser
Herond Browser is a Web browser that prioritizes users’ privacy by blocking ads and cookie trackers, while offering fast browsing speed and low bandwidth consumption. Herond Browser features two built-in key products:
- Herond Shield: an adblock and privacy protection tool;
- Herond Wallet: a multi-chain, non-custodial social wallet.

Herond aims at becoming the ultimate Web 3.0 solution, heading towards the future of mass adoption.
Join our Community!