Discussing the consensus mechanism in Blockchain Technology, we will easily think about Proof of Work (PoW) or Proof of Stake (PoS). However, there is one more term “Proof of Authority” (PoA). This kind of consensus mechanism can achieve consensus in a secure, efficient, and scalable manner, making them suitable for a wide range of applications and use cases by leveraging known and trusted authorities.

This article will introduce to you a comprehensive understanding of Proof of Authority (PoA) on its definition and how it operates.
What is Proof of Authority (PoA)?
Proof of Authority (PoA) is a consensus mechanism used in blockchain networks to validate transactions and secure the network. Unlike Proof of Work (PoW) or Proof of Stake (PoS), which rely on computational power or stake-based voting, PoA relies on the identity and reputation of network validators, known as authorities.
How Does Proof of Authority (PoA) Work?
Here is the step-by-step guide on how the PoA consensus mechanism operates:
Step 1: Selection of Authorities
Authorities are pre-selected and trusted entities responsible for validating transactions and creating new blocks in the blockchain. These authorities are typically known and reputable entities within the network, such as corporations, government agencies, or consortium members.
Step 2: Initialization
The authorities are onboarded onto the network and provided with the necessary credentials and permissions to participate in the consensus process. This may involve identity verification and authentication procedures to ensure the authorities’ trustworthiness.
Step 3: Transaction Submission
Participants submit transactions to the network by broadcasting them to the authorities. Transactions contain details such as sender, recipient, amount, and any additional data required by smart contracts or applications.
Step 4: Transaction Validation
Upon receiving a transaction, the authorities validate its authenticity and integrity based on predefined rules and consensus mechanisms. This validation process ensures that the transaction meets the network’s criteria. For instance, sufficient funds, correct formatting, and compliance with smart contract rules.
Step 5: Block Creation
Once validated, transactions are bundled into blocks by one of the authorities. The order of block creation may be determined by a predetermined rotation schedule or other consensus rules agreed upon by the network participants.
Step 6: Block Propagation
The created block is propagated to other authorities in the network for validation. Each authority independently verifies the integrity and validity of the block by inspecting the transactions, cryptographic signatures, and adherence to consensus rules.
Step 7: Consensus
If the majority of authorities agree that the block is valid, it is added to the blockchain, and consensus is reached. Consensus is achieved through the collective agreement of the authorities, rather than through competitive mining or staking as seen in other consensus mechanisms.
Step 8: Finality and Security
Once added to the blockchain, the block is considered final and cannot be altered or reversed without the consensus of the network authorities. PoA provides security and finality by relying on the trustworthiness and consensus of known and reputable authorities. Therefore, it can mitigate the risk of malicious behavior or attacks.
Step 9: Continued Operation
The process of transaction submission, validation, block creation, and consensus continues as new transactions are submitted to the network. The authorities rotate in creating new blocks, and the blockchain grows sequentially with each validated block added to the chain.
Benefits of Proof of Authority (PoA)
Proof of Authority (PoA) offers several benefits, making it an attractive consensus mechanism for specific blockchain networks, particularly in private, enterprise, and permissioned environments. Let’s discover the advantages of PoA with us!
Enhanced Security
PoA networks benefit from the trustworthiness and reputation of the selected authorities. Since authorities are known and reputable entities within the network, the risk of malicious behavior or attacks is significantly reduced compared to decentralized consensus mechanisms like Proof of Work (PoW) or Proof of Stake (PoS).

Finality
Transactions confirmed by PoA consensus are considered final and cannot be reversed without the consensus of the network authorities. This provides strong guarantees of transaction finality and ensures the immutability of the blockchain, making it suitable for applications where data integrity is critical.
Efficiency and Scalability
PoA networks are often more efficient and scalable than PoW or PoS networks, as they do not require extensive computational resources or energy consumption. PoA consensus can achieve higher transaction throughput and lower latency, making it suitable for enterprise and consortium blockchain solutions with high transaction volumes.
Faster Transaction Processing
PoA networks can process transactions quickly due to the streamlined consensus process involving a predefined set of trusted authorities. This enables faster settlement times and improves the overall user experience, particularly in applications where real-time transaction processing is essential.
Governance and Control
PoA networks offer greater control and governance over the consensus process, as authorities are typically selected and managed by network participants or governing entities. This centralized approach to consensus can be advantageous in scenarios where regulatory compliance, data privacy, and governance requirements are important considerations.
Moreover, PoA consensus allows network organizers to customize governance models and consensus rules according to the specific requirements of the network. This flexibility enables fine-tuning of parameters to suit the needs of different applications and use cases. For example, block creation intervals, authority rotation schedules, and governance mechanisms.
Furthermore, PoA networks are well-suited for applications requiring regulatory compliance, as they offer greater transparency, accountability, and control over network participants and transactions. Authorities can enforce compliance measures such as Know Your Customer (KYC) procedures and transaction monitoring, facilitating regulatory compliance in regulated industries.
Low Barrier to Entry
PoA networks have a low barrier to entry for validators, as participation does not require significant computational resources or stake-based voting. This makes it easier for trusted entities to join the network as authorities, promoting inclusivity and participation in the consensus process.

Drawbacks of Proof of Authority (PoA)
Besides the aforementioned benefits, PoA also has some drawbacks that may limit its suitability for certain blockchain networks and applications. Some of the key drawbacks of PoA include:
Centralization of Authority
PoA networks rely on a predefined set of trusted authorities to validate transactions and secure the network. To explain, this centralization of authority can lead to concerns about concentration of power and control in the hands of a few entities, potentially undermining the decentralized principles of blockchain technology.
Limited Decentralization
PoA networks may have limited decentralization compared to decentralized consensus mechanisms. For example, Proof of Work (PoW) or Proof of Stake (PoS). Since authorities are pre-selected and trusted entities, there may be fewer opportunities for decentralized participation and consensus among network participants.

Risk of Authority Compromise
PoA networks are vulnerable to the compromise of one or more authorities. Consequently, it could result in fraudulent activities such as double spending or transaction censorship. The trustworthiness and integrity of authorities are critical in maintaining the security and reliability of the network.
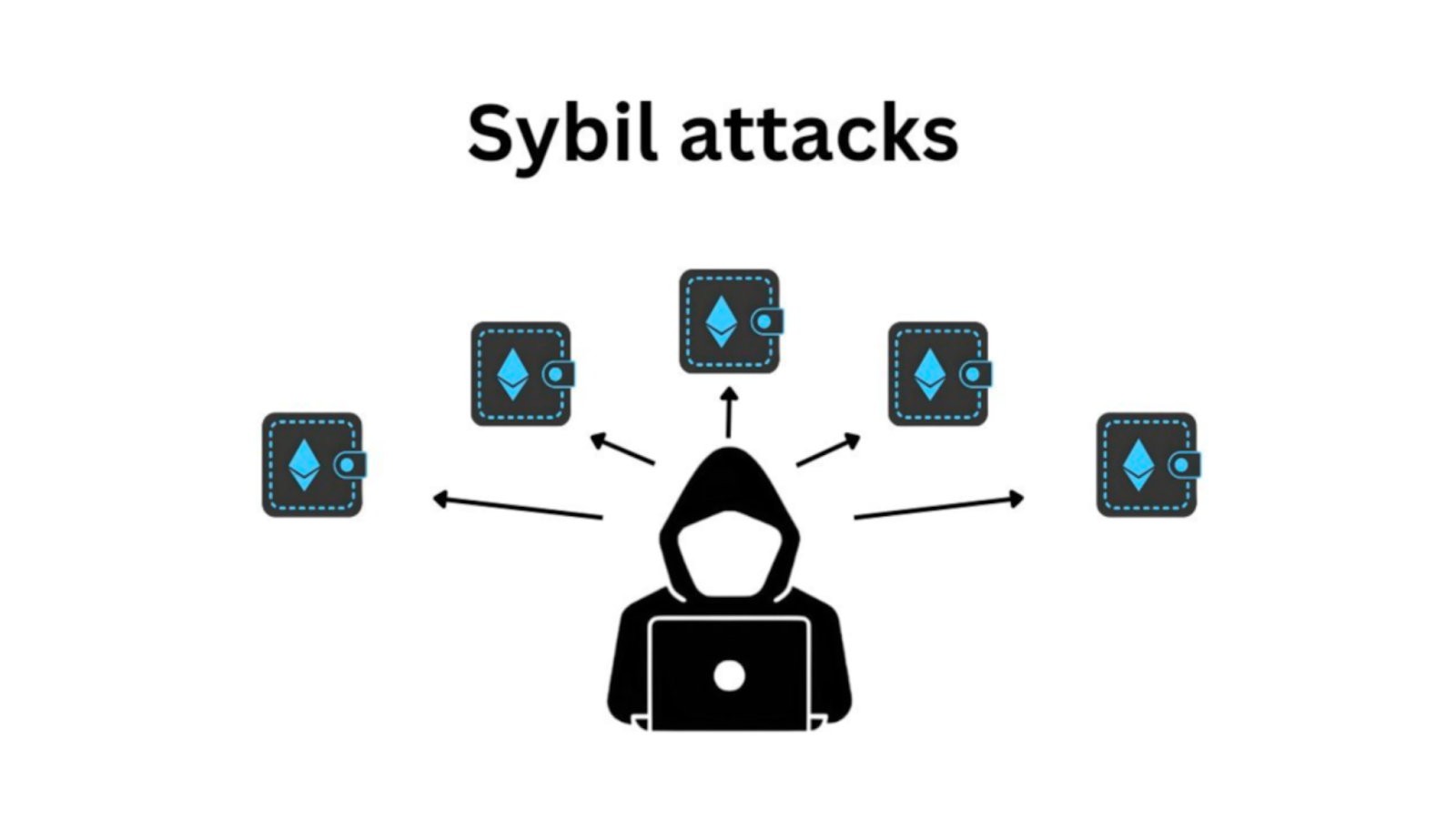
Limited Resistance to Sybil Attacks
PoA networks may be susceptible to Sybil attacks. In more detail, where malicious entities create multiple identities or authorities to manipulate the consensus process. The risk of Sybil attacks can be mitigated through identity verification and authentication procedures. However, it remains a potential vulnerability in PoA networks.
Conclusion
To sum up, Proof of Authority (PoA) provides a practical and efficient consensus mechanism for blockchain networks. Particularly, in environments where identity, governance, and trust are paramount. On the contrary, it also has drawbacks related to centralization, authority compromise, and regulatory concerns. Therefore, network organizers and participants should carefully consider these drawbacks when evaluating the suitability of PoA for specific blockchain networks and applications.
About Herond Browser
Herond Browser is a Web browser that prioritizes users’ privacy by blocking ads and cookie trackers, while offering fast browsing speed and low bandwidth consumption. Herond Browser features two built-in key products:
- Herond Shield: an adblock and privacy protection tool;
- Herond Wallet: a multi-chain, non-custodial social wallet.
Herond aims at becoming the ultimate Web 2.5 solution that sets the ground to further accelerate the growth of Web 3.0, heading towards the future of mass adoption.
Join our Community!



I love how you make complex topics so easy to understand. Well done!
Your blog post was really enjoyable to read, and I appreciate the effort you put into creating such great content. Keep up the great work!