In the world of digitalization, the security of our information is more important than ever. Whether it is protecting personal data from cybercriminals, securing online transactions, or ensuring the privacy of our communications, cryptography plays a pivotal role. But what exactly is cryptography, and how does it work? This fascinating field combines mathematics, computer science, and engineering to create methods that keep our data safe from prying eyes. In this article, we will delve into the fundamentals of cryptography, explore its various types, and understand the mechanisms behind its powerful techniques. Join us as we unravel the secrets of how cryptography safeguards our digital world.
What is Cryptography?
Cryptography is the science and art of securing communication and data from unauthorized access and manipulation. It involves techniques and methods for transforming information into a secure format that only intended recipients can read and understand.
Types of Cryptography
Symmetric-Key Cryptography
In symmetric-key cryptography, the same key is used for both encryption and decryption. This method is efficient and fast but requires the secure exchange and management of keys.
Examples:
- AES (Advanced Encryption Standard): Widely used in various applications, including secure communications and data encryption.
- DES (Data Encryption Standard): An older standard that has largely been replaced by AES due to security vulnerabilities.
- 3DES (Triple DES): An enhancement of DES that applies the encryption process three times to each data block.
Asymmetric-Key Cryptography
Asymmetric-key cryptography uses a pair of keys: a public key for encryption and a private key for decryption. This method facilitates secure key exchange and digital signatures.
Examples:
- RSA (Rivest-Shamir-Adleman): Commonly used for secure data transmission and digital signatures.
- ECC (Elliptic Curve Cryptography): Offers similar security to RSA but with shorter key lengths, making it more efficient.
Hash Functions
Hash functions generate a fixed-size hash value from input data of any size. They are used for data integrity verification, password hashing, and digital signatures.
Examples:
- SHA-256 (Secure Hash Algorithm 256-bit): Widely used in blockchain technology and digital signatures.
- MD5 (Message Digest Algorithm 5): An older hash function with known vulnerabilities, now largely replaced by more secure algorithms like SHA-256.
Digital Signatures
Digital signatures use asymmetric cryptography to verify the authenticity and integrity of a message, software, or document. A digital signature is created using a private key and verified with a public key.
Examples:
- RSA Digital Signatures: Utilizes the RSA algorithm for creating and verifying signatures.
- ECDSA (Elliptic Curve Digital Signature Algorithm): Uses elliptic curve cryptography for creating digital signatures, providing high security with shorter keys.
Public Key Infrastructure (PKI)
PKI is a framework that manages digital keys and certificates for secure communications. It ensures the validity of public keys through trusted Certificate Authorities (CAs).
Quantum Cryptography
Quantum cryptography uses principles of quantum mechanics to achieve secure communication. It aims to leverage quantum bits (qubits) for enhanced security.
Examples:
- Quantum Key Distribution (QKD): A method for securely distributing encryption keys, theoretically immune to all forms of computational attack due to the principles of quantum mechanics.
How cryptography works
Cryptography works by converting readable data, known as plaintext, into an unreadable format, called ciphertext, through various mathematical techniques. This transformation process ensures that only authorized parties can access and understand the information.
In cybersecurity, on the one hand, encryption is the process of converting plaintext into ciphertext using an algorithm and a key. On the other hand, decryption is the reverse process, converting ciphertext back into plaintext using an algorithm and a key. Moreover, besides encryption and decryption, keys are essential to the encryption and decryption processes. They can be symmetric (the same key is used for both processes) or asymmetric (different keys are used for encryption and decryption).
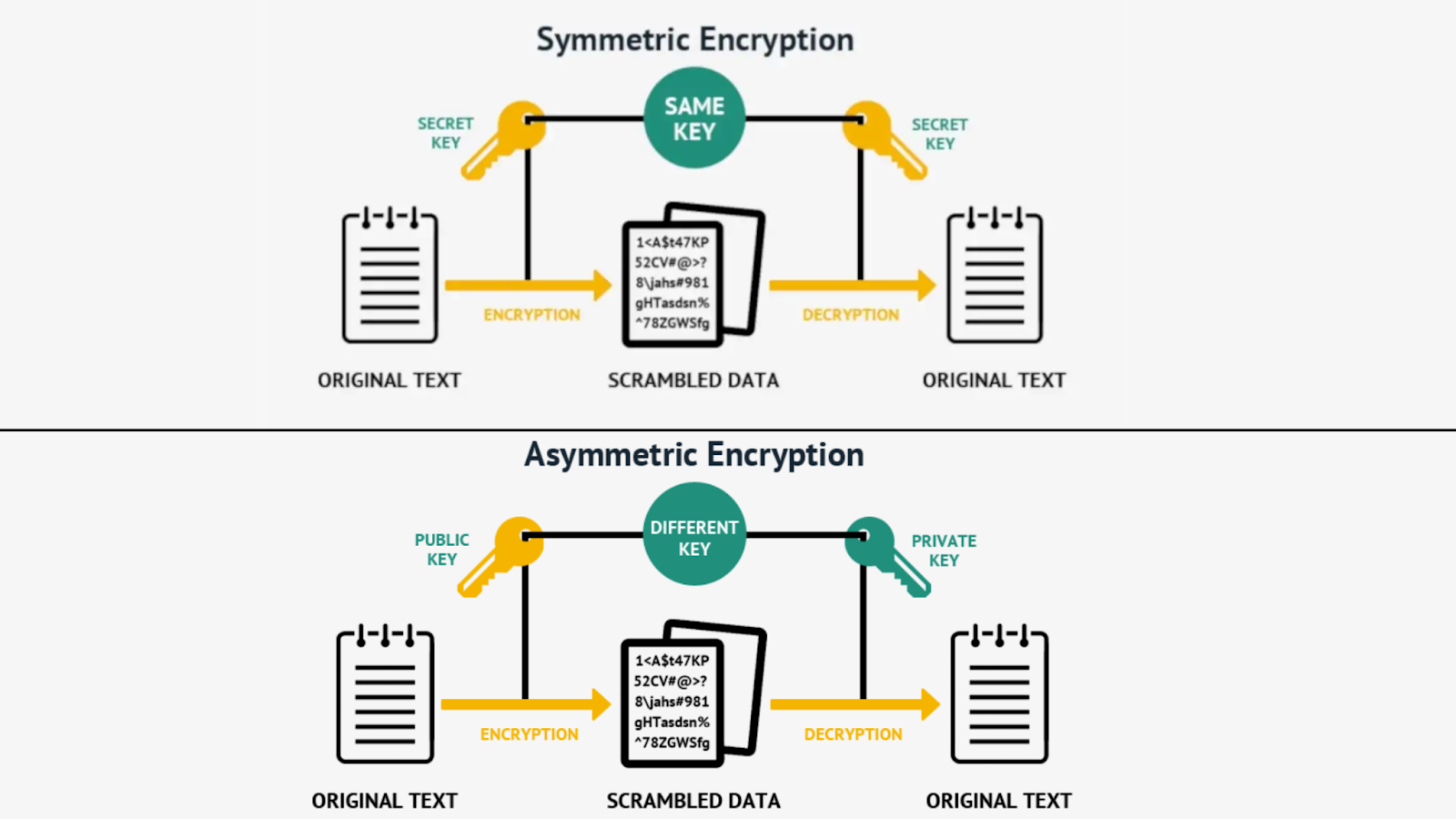
The exact technique used to scramble plaintext into ciphertext defines how cryptography works. Symmetric encryption, asymmetric encryption, blockchain, and digital signatures are some prominent encryption techniques. Hashing, another cryptographic process, is not technically encryption, since it doesn’t use keys.
Importance of Cryptography

Cryptography plays a vital role in ensuring the security and privacy of information in the digital age. Here are some key points highlighting its importance:
Confidentiality
Cryptography ensures that information remains private and accessible only to authorized parties. By encrypting data, it prevents unauthorized access and protects sensitive information from being intercepted or read by malicious actors. For example, online banking transactions use encryption to keep financial information secure.
Data Integrity
Cryptography helps maintain the integrity of data by ensuring that it has not been altered or tampered with during transmission. Hash functions and digital signatures are used to verify that the data received is the same as the data sent. For example, software updates are often verified using cryptographic hashes to ensure they haven’t been modified by hackers.
Authentication
Cryptographic techniques are used to verify the identities of users, devices, and systems. This helps establish trust and prevent unauthorized access. For example, two-factor authentication (2FA) uses cryptographic methods to confirm a user’s identity by requiring two forms of verification.
Non-repudiation
Cryptography ensures that a party cannot deny the authenticity of their signature on a document or the sending of a message. Digital signatures provide proof of origin and integrity, making it difficult for someone to repudiate their actions. For instance, in legal and financial transactions, digital signatures are used to provide a verifiable and legally binding record of agreements.
Secure Communication
Cryptography enables secure communication over potentially insecure channels such as the internet. It ensures that messages and data are encrypted and can only be decrypted by the intended recipient. For instance, secure email protocols like PGP (Pretty Good Privacy) encrypt email content to protect against eavesdropping.
Protection Against Cyber Threats
Cryptography is essential in protecting against various cyber threats, including hacking, phishing, and data breaches. It forms the foundation of many security protocols that safeguard information and communications. To explain, SSL/TLS protocols use cryptography to secure web traffic, protecting against man-in-the-middle attacks and ensuring secure browsing.
Enabling Digital Transformation
As businesses and services move online, cryptography is essential for enabling secure digital transactions and communications. It supports the development of new technologies and services by providing the security necessary for widespread adoption. For instance, e-commerce platforms rely on cryptography to protect customer information and payment details, facilitating secure online shopping experiences.
Conclusion
In short, cryptography is a cornerstone of modern digital security, providing essential mechanisms to protect our data, communications, and transactions from unauthorized access and malicious attacks. By transforming readable information into secure formats through various algorithms and techniques, cryptography ensures confidentiality, integrity, authentication, and non-repudiation in our digital interactions. From symmetric and asymmetric encryption to hash functions and digital signatures, the diverse tools of cryptography work together to create a secure environment in our increasingly interconnected world. Understanding the principles and applications of cryptography empowers us to appreciate the underlying technology that safeguards our digital lives and to make informed decisions about our online security. As we continue to advance in the digital age, the importance of cryptography will only grow, reinforcing its role as a fundamental pillar of trust and security.
About Herond Browser
Herond Browser is a Web browser that prioritizes users’ privacy by blocking ads and cookie trackers, while offering fast browsing speed and low bandwidth consumption. Herond Browser features two built-in key products:
- Herond Shield: an adblock and privacy protection tool;
- Herond Wallet: a multi-chain, non-custodial social wallet.
Herond aims at becoming the ultimate Web 3.0 solution, heading towards the future of mass adoption.
Join our Community!