Public-key cryptography serves as a foundational building block for various cryptographic applications, providing secure communication, data protection, authentication, and access control in digital environments. Therefore, its widespread adoption has contributed to the development of secure and trusted systems for exchanging information and conducting transactions over the internet.
Within the Public-Key cryptography, there are two main keys including Public and Private Ones. This article aims to provide you a closer look into the purposes of these two keys and discuss their differences within the asymmetric cryptography. Let’s explore!
What is a Public Key?
A public key is a component of asymmetric cryptography, also known as public-key cryptography. It is a cryptographic key that is used to encrypt data or verify digital signatures. In more detail, the public key is freely shared and distributed, while the corresponding private one is kept secret and known only to its owner.
What is a Private Key?

A private key is a component of asymmetric cryptography, also known as public-key cryptography. It is a cryptographic key that is kept secret and known only to its owner. In a public-private key pair, the private one is paired with a corresponding public one, with the private one being used for decryption and digital signatures creation.
What is Public-Key Cryptography?

Public-key cryptography, also known as asymmetric cryptography, is a cryptographic approach that utilizes a pair of keys for secure communication and data exchange. These keys consist of a public and a private key, both of which are mathematically related but serve different purposes and are kept secret from each other.
Purposes of Public-Key Cryptography
Secure Communication
One of the primary purposes of public-key cryptography is to facilitate secure communication over insecure channels such as the internet. By using asymmetric encryption techniques, participants can exchange encrypted messages without needing to share a secret key beforehand.
Data Protection
It ensures the confidentiality and integrity of sensitive data by allowing it to be encrypted using recipient’s public keys. Only the recipient with the corresponding private key can decrypt the data, protecting it from unauthorized access or modification.
Digital Signatures
It enables the creation and verification of digital signatures, which are used to authenticate the origin and integrity of digital messages or documents. Digital signatures provide assurance that a message was created by a particular sender and has not been tampered with in transit.
Authentication
It can be used for authentication purposes, such as verifying the identity of a user or a server. By proving possession of private keys corresponding to a known public one, individuals or entities can authenticate themselves securely in digital transactions.
Key Exchange
It facilitates secure key exchange protocols, allowing participants to establish shared secret keys for symmetric encryption without needing to transmit the keys over insecure channels. This is commonly used in protocols like SSL/TLS for secure web communication.
Non-Repudiation
It provides non-repudiation, meaning that a sender cannot later deny having sent a message or created a digital signature. Since only the sender possesses the private keys used to create the signature, its authenticity can be verified by anyone with access to the sender’s public one.
Secure Access Control
Public-key cryptography can be used for secure access control mechanisms, such as SSH pairs for secure remote login or digital certificates for user authentication in web browsers. It ensures that only authorized users with the corresponding private keys can access protected resources.
How Public Key Cryptography Works
Overall, compared to the symmetric cryptographic, it is an asymmetric cryptography. In more detail, Public-Private Key Cryptography works thanks to two main keys including a public key to encrypt messages and a private one to decode them.
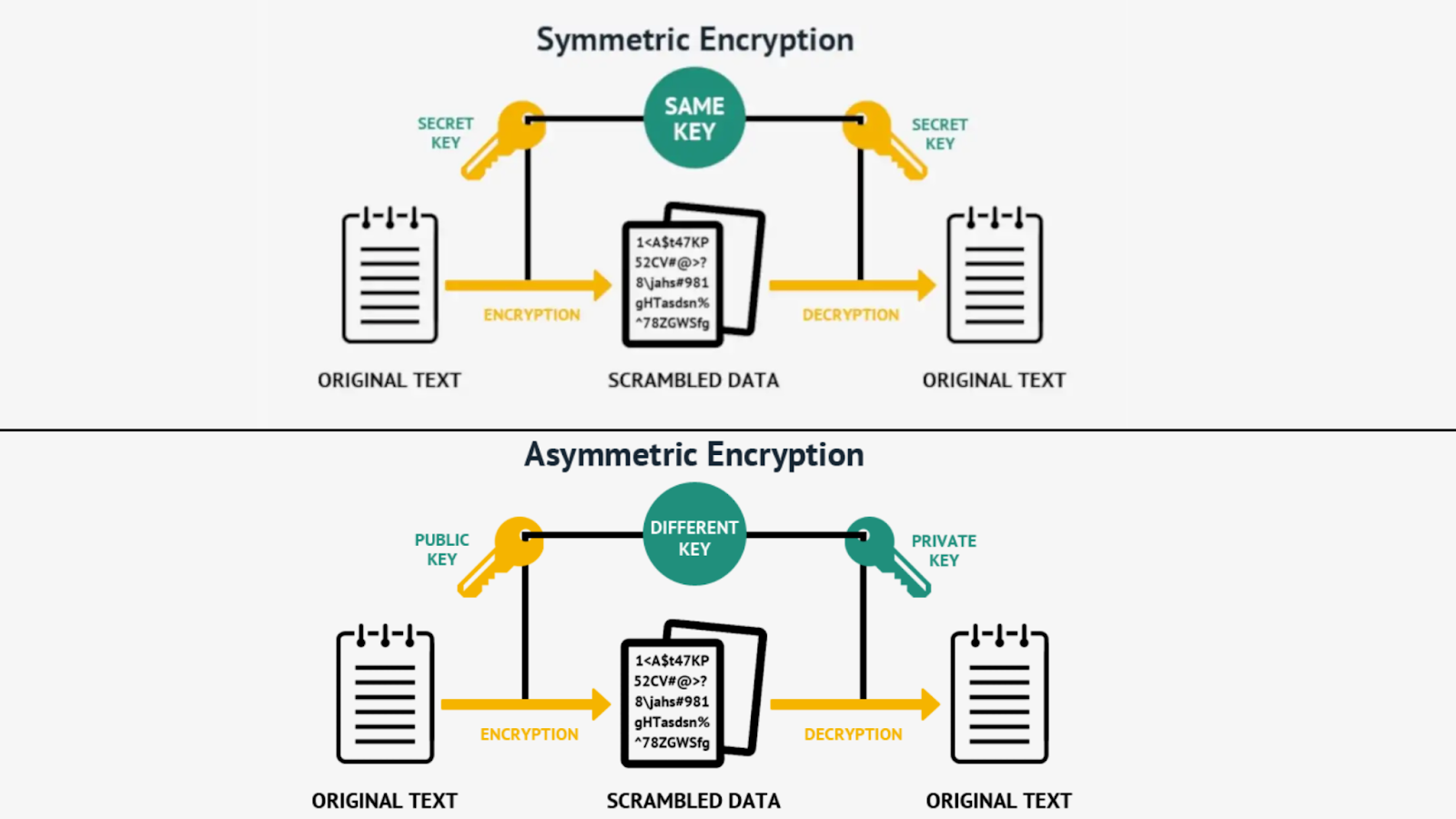
Here’s a step-by-step guide to understanding how the asymmetric cryptography works:
- Key Pair Generation: The process starts with each participant generating a pair of cryptographic keys: a public and a private key. These keys are mathematically related, but it is computationally infeasible to derive one key from the other.
- Public Key Distribution: Each participant freely shares their public key with others. It can be distributed openly and does not need to be kept secret.
- Encryption: The sender’s data is encrypted using the recipient’s public key. Then, the sender’s data is sent to the recipient.
- Decryption: The recipient decrypts the message using their own private key.
- Authentication: This kind of cryptography can also be used for authentication purposes. For example, the client can verify the server’s identity by confirming that the presented public key matches the one it expects from the server. Therefore, this ensures that the client is communicating with the intended server and not an impostor.
Public Key vs Private Key: Main Differences
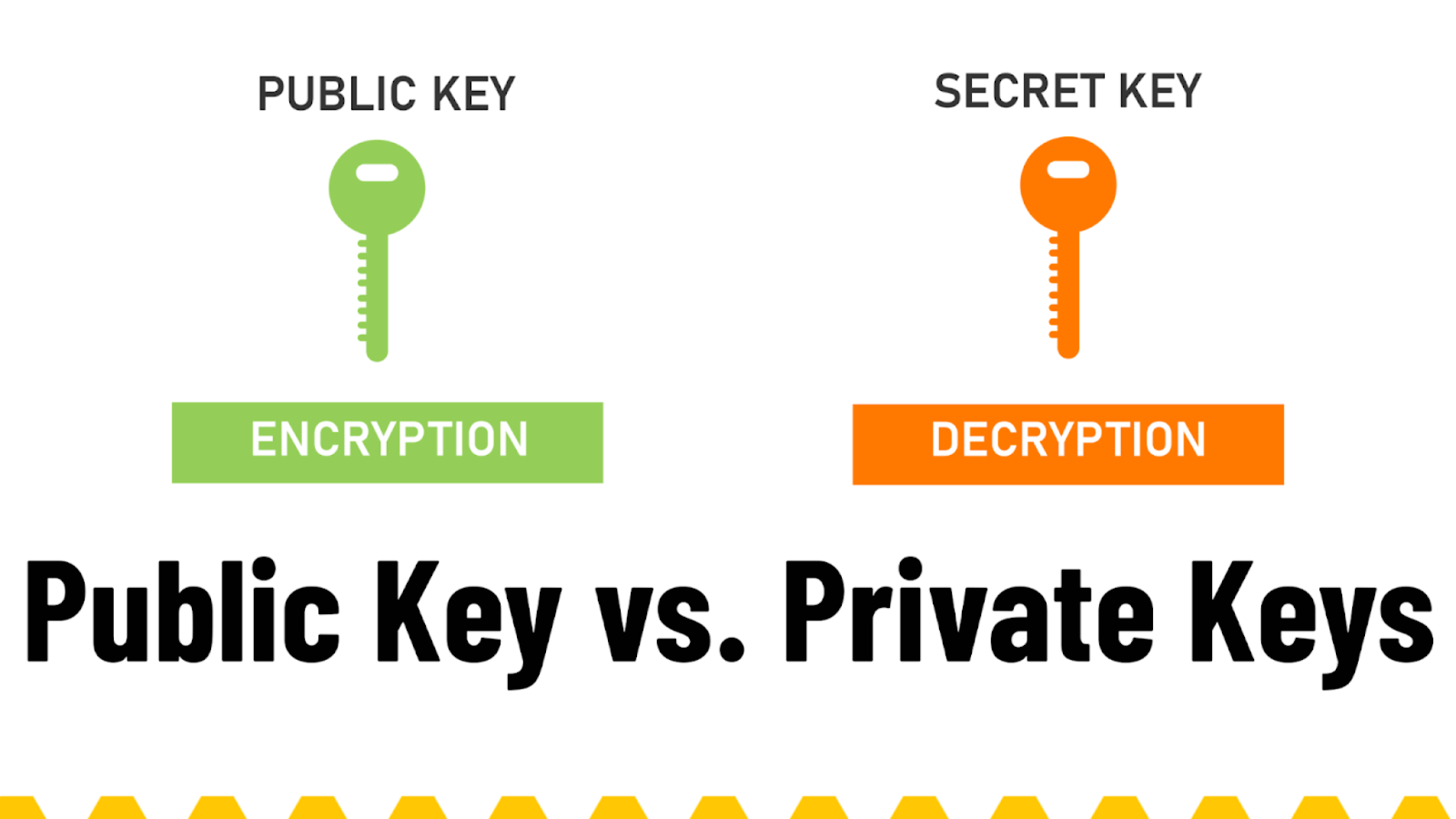
Here are some main differences between two keys in the asymmetric cryptography:
| Criteria | Private Key | Public Key |
| Function | The private key is used for decryption and digital signatures creation. | The public key is used for encryption and digital signatures verification. |
| Secrecy | The private key is kept secret and known only to its owner. It must be securely stored and never shared with anyone else. | The public key is freely shared and distributed to anyone who needs to communicate securely with the key holder. It can be openly published and does not need to be kept secret. |
Conclusion
To sum up, the main difference between two crypto keys lies in their secrecy, usage, and roles within asymmetric cryptography. From a closer inspection, the private one is kept secret and used for decryption and digital signatures creation, while the public one is openly shared and used for encryption and digital signatures verification. Together, they form a secure communication mechanism in various cryptographic applications.
About Herond Browser
Herond Browser is a Web browser that prioritizes users’ privacy by blocking ads and cookie trackers, while offering fast browsing speed and low bandwidth consumption. Herond Browser features two built-in key products:
- Herond Shield: an adblock and privacy protection tool;
- Herond Wallet: a multi-chain, non-custodial social wallet.
Herond aims at becoming the ultimate Web 2.5 solution that sets the ground to further accelerate the growth of Web 3.0, heading towards the future of mass adoption.
Join our Community!



The positivity and optimism conveyed in this blog never fails to uplift my spirits Thank you for spreading joy and positivity in the world
Your blog is quickly becoming one of my go-to resources. Keep it up!
Your blog post was really enjoyable to read, and I appreciate the effort you put into creating such great content. Keep up the great work!